274
The cybersecurity industry is facing an unprecedented workforce shortage that grew nearly 10 percent this past year, according to a study from nonprofit organization ISC2.
Some analysts employed in the industry aren’t fully equipped with the ski
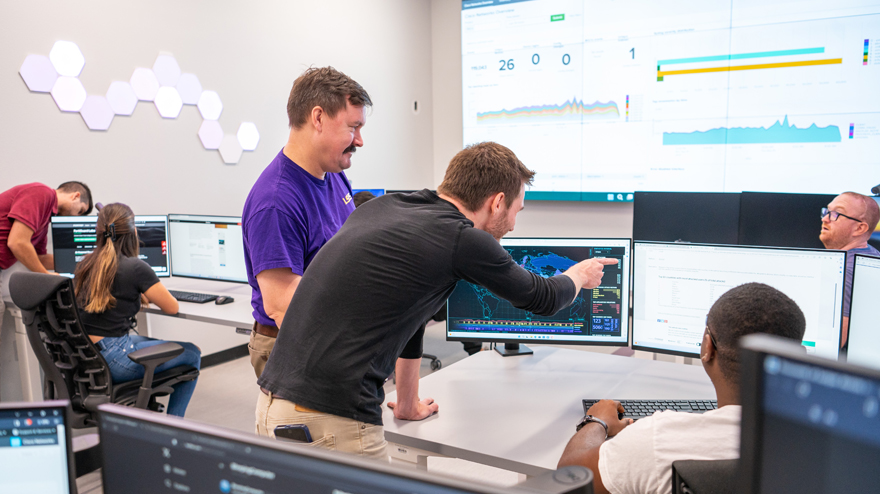
Ched Wiggins, Security Operations Center lead, and James Jackson, associate director of IT Security, analyze data in a populated Security Operations Center on LSUS’s campus in this photo illustration. LSUS is hiring students to fill roles as cybersecurity analysts in this on-campus SOC to identify and respond to threats to LSUS’s network.
CREDIT: Photo illustration courtesy of LSUS


